Ever wonder what actually happens when you click a link? It feels instant, but a complex process is taking place. To understand cybersecurity networking basics, we first need a blueprint for how computers talk to each other. That blueprint is the OSI (Open Systems Interconnection) Model. This guide will make the OSI model explained simple for you.
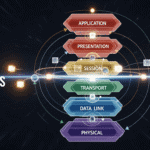
Think of it as a seven-story office building. For a package of data to be sent, it must pass down through every floor, with each floor adding its own label. Let’s break down the 7 layers of networking as defined by the OSI Model.
The 7 Layers of the OSI Model
We’ll start from the top (Layer 7) where you work, and go down to the bottom (Layer 1) which is the physical hardware.
Layer 7: The Application Layer
This is the only layer you directly interact with. The Application Layer provides network services to your software, like a web browser or email client. When you use Chrome to visit a website, you’re using protocols at this layer.
- Examples: HTTP, HTTPS, SMTP, FTP.
Layer 6: The Presentation Layer
The Presentation Layer acts as a universal translator. Its main job is to handle data formatting, compression, and encryption. It ensures that data sent from one system can be read by another by converting it into a standard format.
- Examples: SSL/TLS (for encryption), JPEG, ASCII.
Layer 5: The Session Layer
The Session Layer is the conversation manager. It is responsible for opening, managing, and closing the communication “session” between two devices. It makes sure the connection stays open long enough to transfer all the data and then closes it efficiently.
Layer 4: The Transport Layer
The Transport Layer is responsible for end-to-end communication and error control. It breaks up data into smaller chunks called segments. It also chooses how reliably that data needs to be sent.
- Examples: TCP (Transmission Control Protocol) is the reliable option, ensuring all data arrives in order. UDP (User Datagram Protocol) is faster but less reliable.
Layer 3: The Network Layer
The Network Layer is the “director of traffic.” Its job is to handle the routing of data packets across different networks to their final destination. This is where logical addressing happens.
- Examples: IP (Internet Protocol) and routers operate at the network layer.
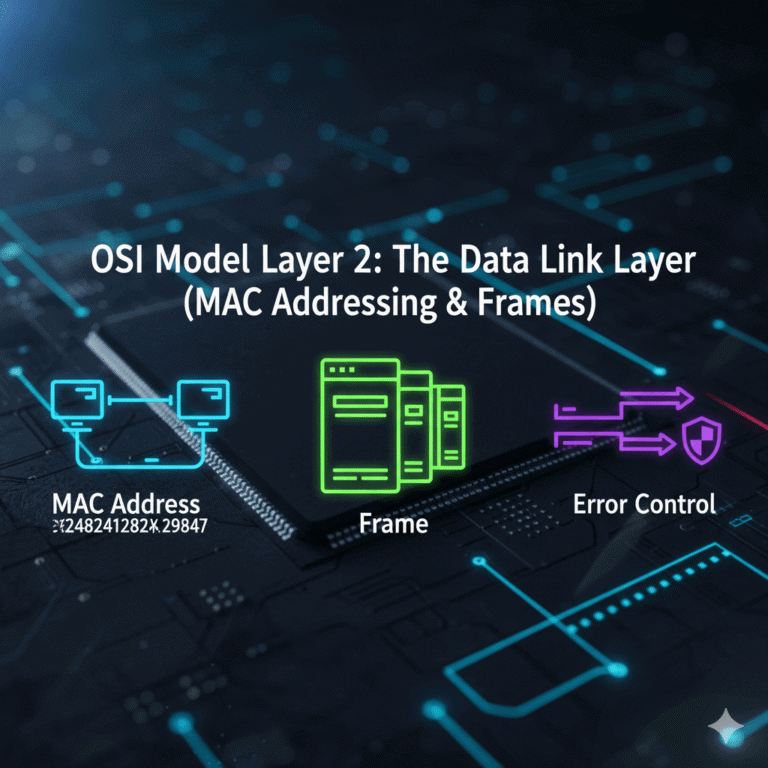
Layer 2: The Data Link Layer
The Data Link Layer manages data transfer between two devices on the same local network. It handles the hop-by-hop delivery from your computer to your router. This is where physical addressing (MAC addresses) occurs.
- Examples: MAC Addresses, Ethernet, Wi-Fi, Network Switches.
Layer 1: The Physical Layer
The Physical Layer is all about the hardware. It is the actual, physical stuff that carries the signal, like cables and radio waves. This layer is responsible for transmitting the raw bits (1s and 0s) over a physical medium.
- Examples: Ethernet Cables, Fiber-Optic Cables, Wi-Fi radio waves.
Why the OSI Model Matters for Cybersecurity
Understanding these 7 layers is crucial because different cyber-attacks target different layers. A DDoS attack might flood the Network Layer (Layer 3), while a phishing attack starts at the Application Layer (Layer 7). Knowing this model helps you understand how tools like firewalls and Nmap work to protect networks.
Ready to get your hands dirty? Subscribe to CyberTerminal to stay updated!
[INSERT_ELEMENTOR id=”1346″]