OSI Model Layer 1: The Physical Layer (Cables, Signals & Bits)

We’ve completed an incredible journey through the OSI Model! We’ve seen applications create data, the Presentation Layer (Layer 6) format…

We’ve completed an incredible journey through the OSI Model! We’ve seen applications create data, the Presentation Layer (Layer 6) format…
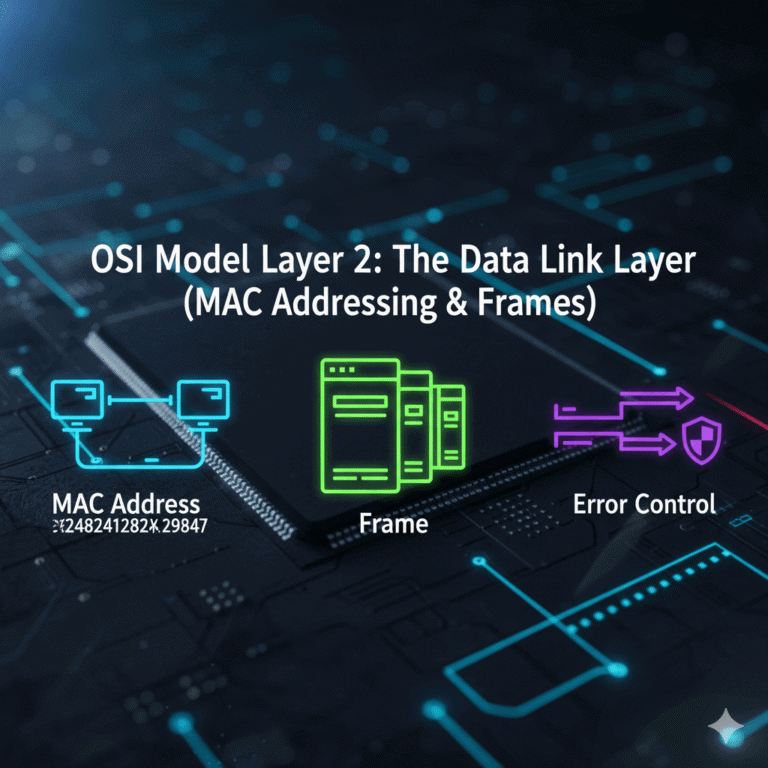
We’ve covered a lot in our OSI Model series! We’ve seen how the Network Layer (Layer 3) uses IP addresses…

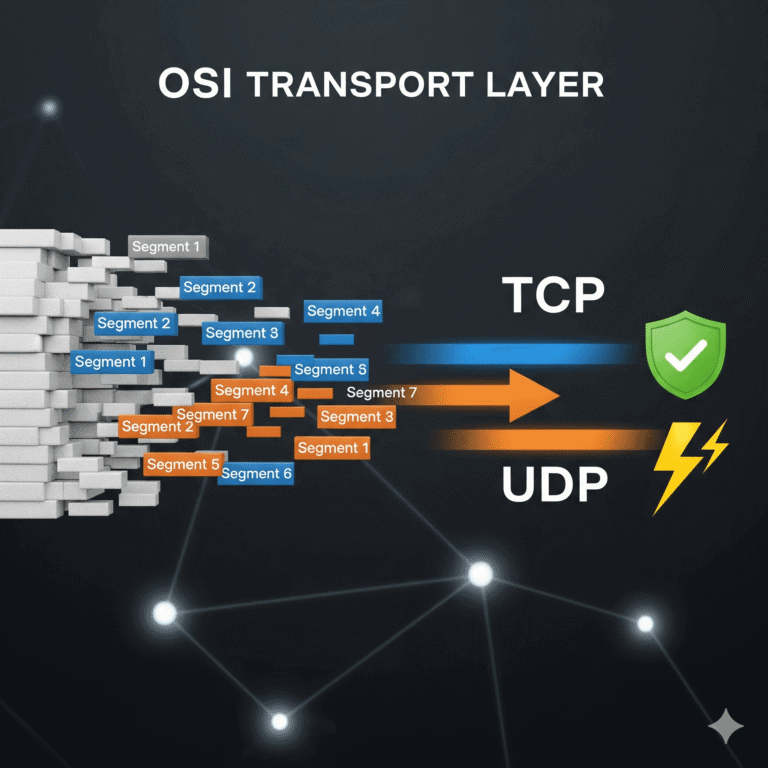
In our last post, we saw how the Transport Layer (Layer 4) prepares our data for its end-to-end journey. But…
In our last post, we saw how the Session Layer (Layer 5) establishes and manages the conversation between two applications.…

In our last post, we explored how the Presentation Layer (Layer 6) acts as a universal translator, formatting our data…
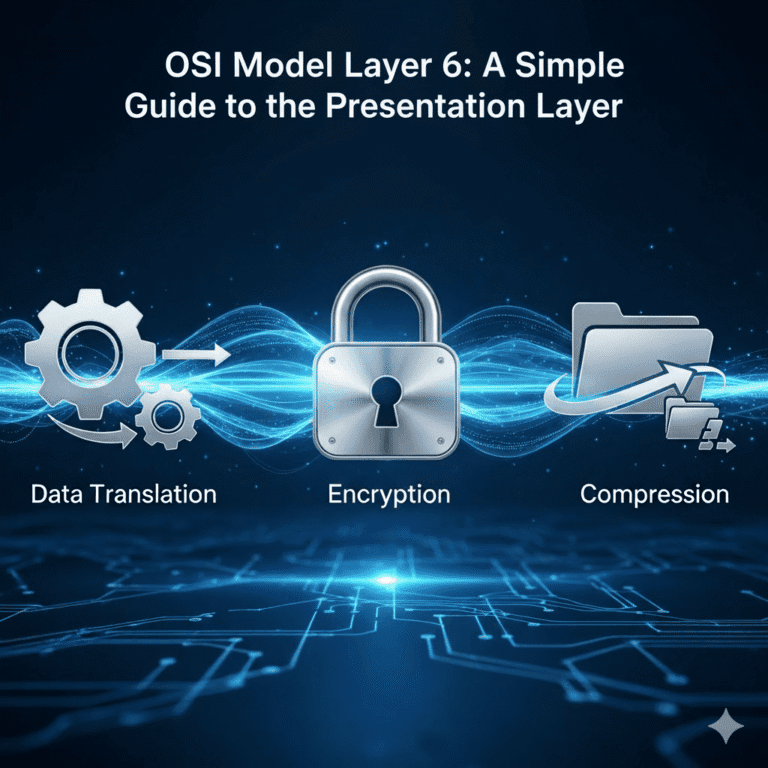
Have you ever wondered how your computer securely sends information that any other computer can understand, regardless of the brand…

In our last article, we introduced the OSI Model as a seven-story blueprint for network communication. We took a quick…
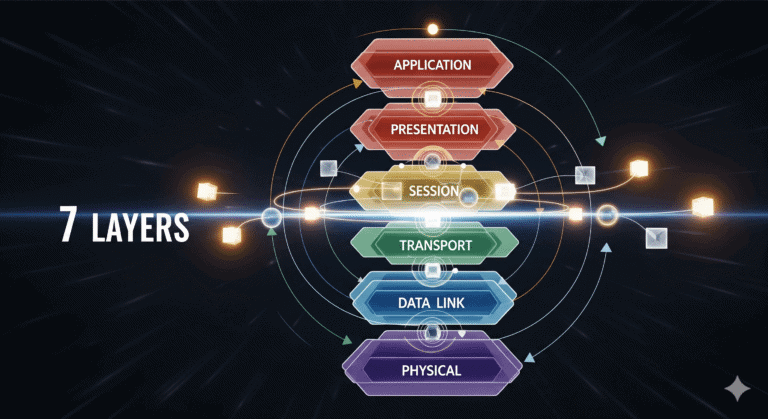
Ever wonder what actually happens when you click a link? It feels instant, but a complex process is taking place.…

You’ve read the roadmap and you’re ready to start your journey into cybersecurity, but one question looms large: “Which certification…
What is a hacker’s single most effective tool? It’s not a complex piece of code or a supercomputer. It’s the…