What is a Brute Force Attack? (A Simple Explanation & How to Stop It)
Imagine a thief trying to open a bicycle lock. Instead of skillfully picking it, they simply sit down and try…

Imagine a thief trying to open a bicycle lock. Instead of skillfully picking it, they simply sit down and try…
Before you can understand how a cyberattack works, you first need to understand the roads it travels on. Every action…
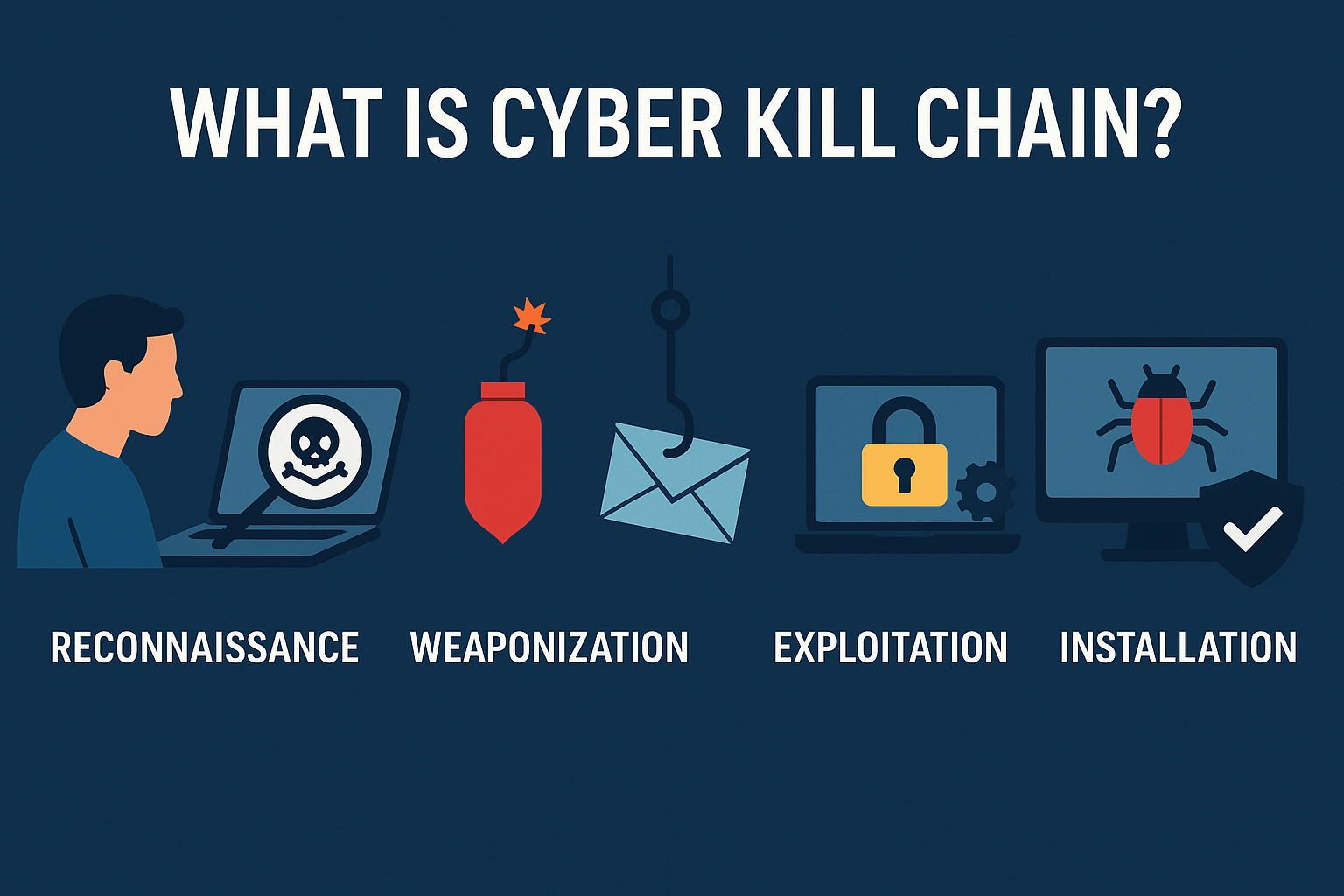
A successful cyberattack isn’t a single event; it’s a carefully planned campaign with multiple, distinct stages. To defend against an…
Have you ever connected to the free Wi-Fi at a coffee shop, airport, or hotel? It’s convenient, but it can…

In our previous guides, we’ve talked about the dangers of phishing attacks and the importance of creating strong passwords. But…
In our last guide, we explored the dangerous world of malware, from viruses and worms to ransomware. The #1 tool…
You’ve probably heard someone say, “I think my computer has a virus!” While they might be right, “virus” is just…

In our last guide, What is Phishing?, we explained how hackers use deceptive messages to trick you into giving up…

You’ve likely heard the term “phishing” before, but what does it actually mean? It’s more than just a spam email;…

Who Are Black Hat Hackers? A Look at the Bad Guys of Cybersecurity In our previous posts, we’ve explored the…