Types of Cloud Computing Models Explained Simply
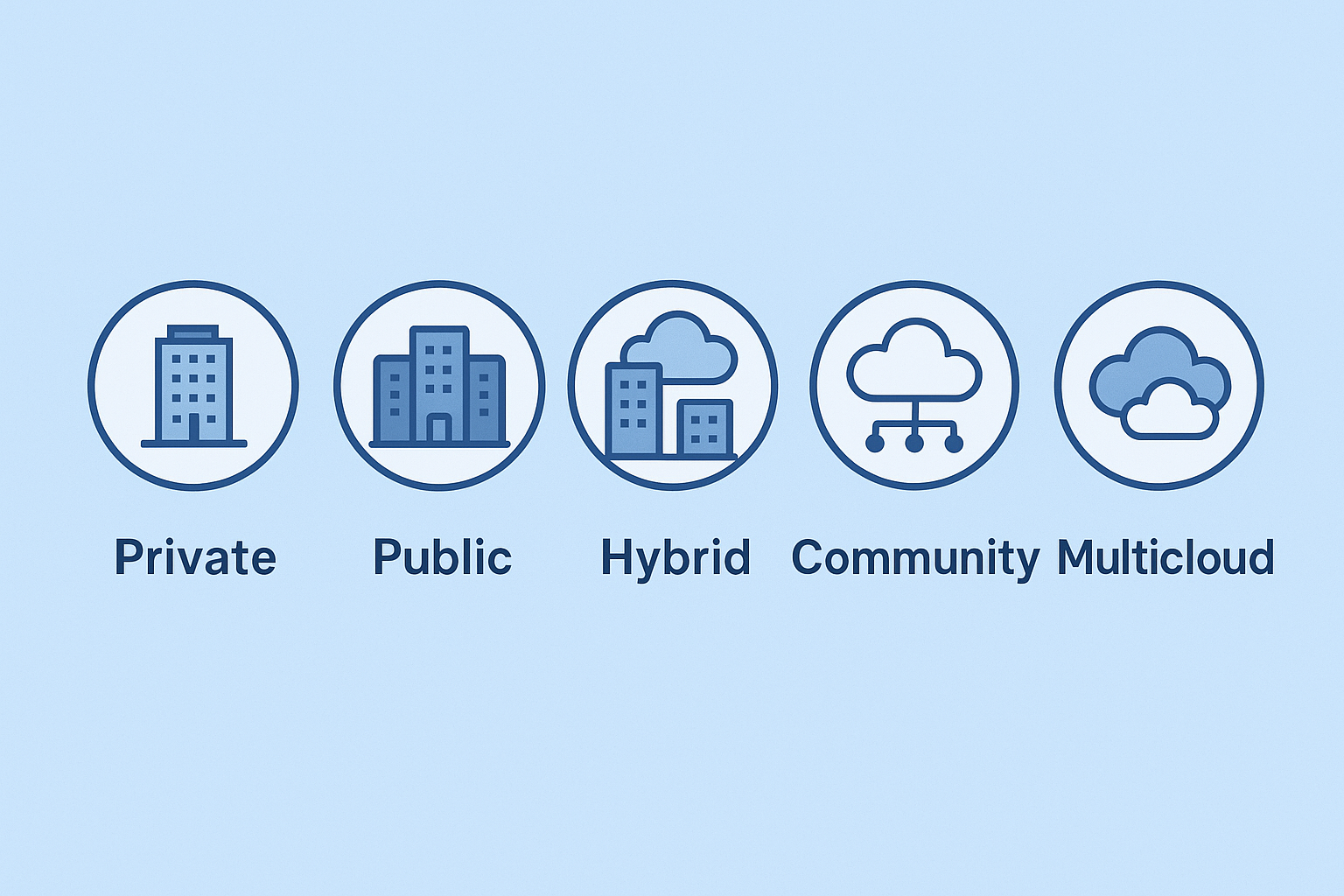
The world of cloud computing is filled with acronyms. IaaS, PaaS, SaaS, DBaaS, Hybrid, Multicloud—it can feel like learning a new language. But understanding this language is the key to making smart decisions about technology, security, and architecture. Consider this your definitive translation guide. In this article, we will provide clear, practical definitions for every […]
What is Cloud Computing? Explained with Pros & Cons
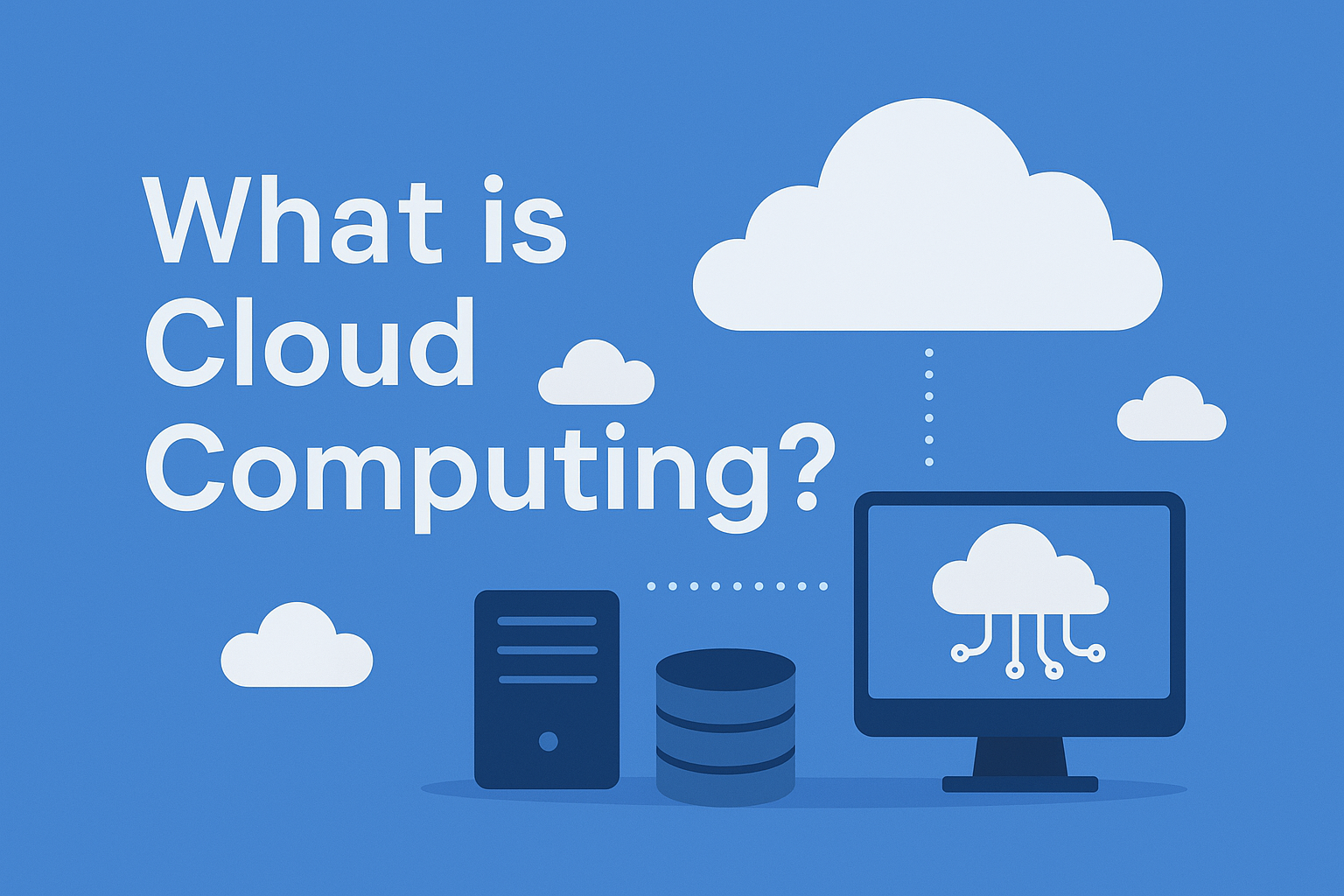
“The Cloud” is one of the most dominant terms in technology, but what does it actually mean to move to the cloud? Is it always the right decision? While the cloud offers incredible power, using it is a strategic choice with both massive benefits and critical trade-offs. This article will serve as your first clear-headed […]
What are White Hat Hackers? A Guide to Ethical Hacking

What are White Hat Hackers? A Look at the Good Guys of Cybersecurity In our last post, we met the three main players in the hacking world. Now, it’s time to put on the white hat and take a closer look at the heroes of the story: the ethical hackers. So, what does it actually […]
Types of Hackers: White Hat, Black Hat, & Grey Hat
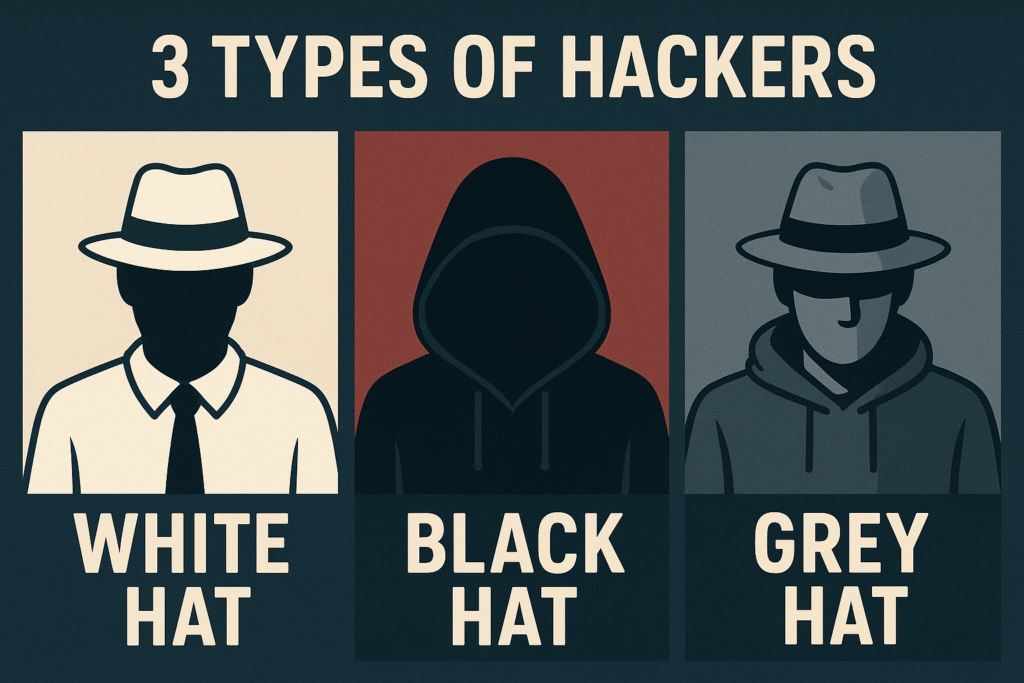
White Hat, Black Hat, Grey Hat: So, What’s the Deal with Hackers? Let’s be honest, when you hear the word “hacker,” you probably picture a shadowy figure in a dark room, glued to a screen full of scrolling green text. It’s the classic movie villain, right? But what if I told you that’s only one […]
The CIA Triad in Cybersecurity: A Simple Explanation

Understanding the 3 Core Pillars of Cybersecurity If you’ve ever wondered what cybersecurity professionals are actually trying to accomplish, it all comes down to three fundamental goals. These principles are the foundation for every security tool, policy, and action. Think of them as the constitution for protecting the digital world.This foundational concept is known as […]
What is CyberSecurity? The Ultimate Guide for Beginners (2025)

You’ve seen the headlines. You’ve probably even received a suspicious SMS about your electricity bill or a strange UPI payment request. In our hyper-connected world of 2025, where everything from our banking to our social lives happens online, our digital world is constantly under siege. The shield that protects us, our data, and our national […]
