We’ve covered a lot in our OSI Model series! We’ve seen how the Network Layer (Layer 3) uses IP addresses to route data packets across vast global networks. But what happens when that data packet finally reaches its destination network? How does it make the crucial, final hop from one device to the very next device on your local network, like from your computer to your Wi-Fi router?
That precise, local delivery is the specialty of Layer 2: The Data Link Layer.
Think of the Data Link Layer as the highly efficient local delivery manager for your network. If the Network Layer provides the global GPS to get your package to the right city, the Data Link Layer acts like the local delivery truck, ensuring the package gets to the correct house (device) on a specific street (local network segment). This layer is fundamental for smooth, error-free communication between directly connected devices.
Understanding the Data Link Layer’s Key Functions
The Data Link Layer is often conceptually split into two sub-layers to handle its diverse tasks:
- Logical Link Control (LLC): This upper sub-layer manages multiplexing of network protocols and handles local error and flow control.
- Media Access Control (MAC): This lower sub-layer is famous for physical addressing (MAC addresses) and controlling how devices share the network’s physical medium.
Let’s dive into its essential responsibilities:
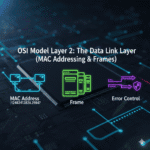
1. Physical Addressing: The Unique MAC Address
Every network-capable device has a unique, hard-coded identifier known as a MAC address (Media Access Control address). This 48-bit (or 64-bit for EUI-64) address is permanently embedded into your device’s network interface card (NIC) by the manufacturer.
- IP vs. MAC: While an IP address is a logical address that can change (like your home’s street address), a MAC address is a physical address that is fixed to your hardware (like the unique serial number of your computer’s network card).
MAC addresses are crucial for communication only within the same local network segment. For instance, when your laptop sends data to your printer on the same Wi-Fi network, it uses the printer’s MAC address to locate it precisely.
2. Framing: Packaging Data for Local Delivery
The Data Link Layer receives packets from the Network Layer and encapsulates them into new units called frames. Think of a frame as a specialized envelope for local delivery.
Each frame has a specific structure:
- Header: Contains vital information, most notably the source and destination MAC addresses.
- Payload: This is where the Network Layer packet (the actual data) resides.
- Trailer: Includes mechanisms for error detection.
This framing process ensures that the data package is correctly addressed for its local hop and includes checks for integrity.
3. Local Error Detection and Correction
While higher layers (like the Transport Layer) handle end-to-end error control, the Data Link Layer performs critical error detection for transmissions over a single network link.
It uses techniques such as Cyclic Redundancy Check (CRC) within the frame’s trailer. If an error is detected as a frame travels from one device to the very next, the Data Link Layer can request a retransmission, ensuring data integrity for that specific local hop.
4. Local Flow Control
Just like major highways need traffic management, so do local network links. The Data Link Layer implements flow control to prevent a fast-sending device from overwhelming a slower receiving device on the same local segment. This ensures that data is transmitted at a manageable rate, preventing buffer overflows and loss of information.
5. Media Access Control (Sharing the Network)
When multiple devices share the same physical transmission medium – whether it’s a shared Ethernet cable (less common now with switches) or the airwaves of a Wi-Fi network – there must be rules to prevent them from “talking over” each other.
The MAC sub-layer manages media access control, defining how and when devices can transmit data without causing collisions. Popular methods include:
- CSMA/CD (Carrier Sense Multiple Access with Collision Detection): Historically used in older Ethernet networks. Devices “listen” before transmitting and stop if a collision is detected.
- CSMA/CA (Carrier Sense Multiple Access with Collision Avoidance): Used in modern Wi-Fi networks. Devices try to avoid collisions before they happen, as detecting them is harder wirelessly.
Conclusion: The Essential Local Network Manager
The Data Link Layer is the meticulous local manager of your network. By uniquely identifying devices with MAC addresses, carefully packaging data into frames, performing local error checks, controlling data flow, and arbitrating access to the shared medium, it ensures the reliable and efficient transfer of data between adjacent devices. It’s the unsung hero that makes your local network connections seamless.
We’ve now seen how data is addressed and routed globally, and how it reliably moves locally. But what about the actual, raw electrical signals, light pulses, or radio waves that carry this information? That’s the fundamental, physical task of our final layer, Layer 1: The Physical Layer. Join us for the thrilling conclusion of our OSI Model series!
Ready to get your hands dirty? Subscribe to CyberTerminal to stay updated!
[INSERT_ELEMENTOR id=”1346″]