What is Social Engineering? (The Art of Human Hacking)
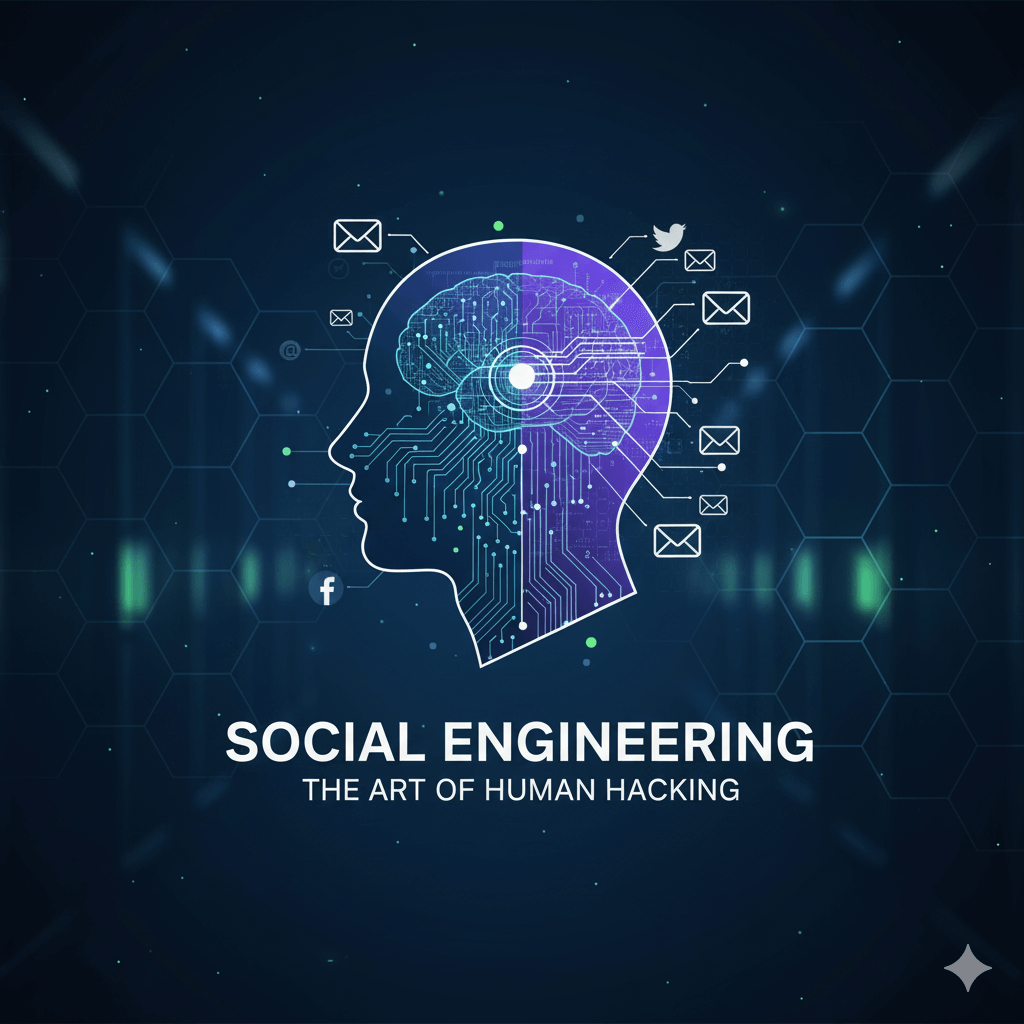
What is a hacker’s single most effective tool? It’s not a complex piece of code or a supercomputer. It’s the human mind. The art of exploiting human psychology to bypass security is called Social Engineering, and it’s often the first step in a major cyberattack. In our previous lessons, we’ve talked about what malware is […]
What is the Cyber Kill Chain?
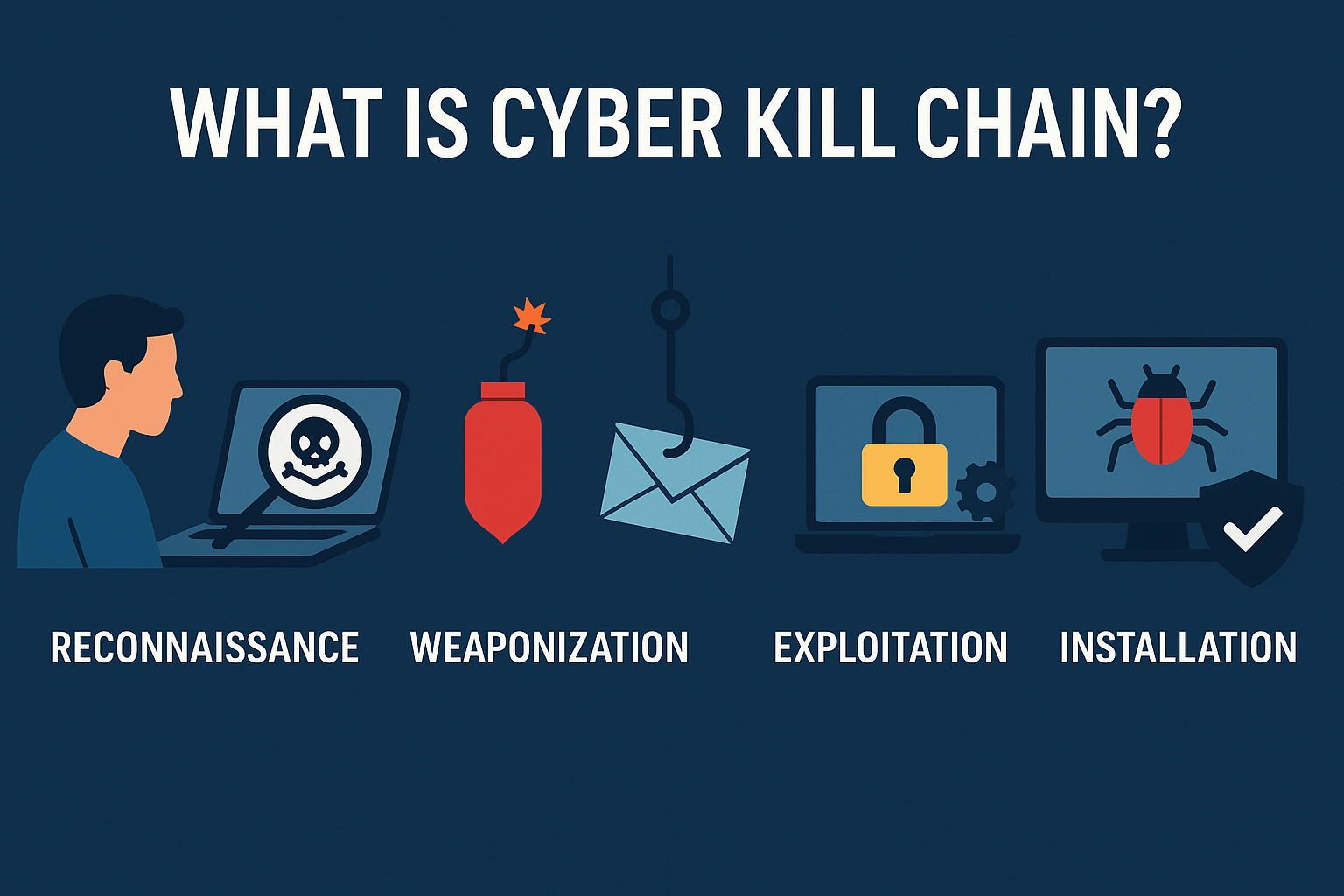
A successful cyberattack isn’t a single event; it’s a carefully planned campaign with multiple, distinct stages. To defend against an enemy, you must first understand how they think and operate. This is where the Cyber Kill Chain comes in. The Cyber Kill Chain is a framework originally created by defense company Lockheed Martin that outlines […]
What is 2FA? A Simple Guide to Securing Your Accounts

In our previous guides, we’ve talked about the dangers of phishing attacks and the importance of creating strong passwords. But what happens if a criminal manages to steal your password anyway? In today’s world of massive data breaches, this is a constant risk. This is where your most powerful defense comes into play: Two-Factor Authentication […]
What is Antivirus Software? A Simple Guide to How It Works
In our last guide, we explored the dangerous world of malware, from viruses and worms to ransomware. The #1 tool in our defensive arsenal against these threats is antivirus software. But what is it, and how does it actually protect your devices? Many people think of it as a simple “virus scanner,” but modern antivirus […]
What is Malware? (A Simple Explanation & Common Types)
You’ve probably heard someone say, “I think my computer has a virus!” While they might be right, “virus” is just one piece of a much larger puzzle. The correct umbrella term for all malicious software is malware. Understanding this threat is fundamental to staying safe online. So, what is malware, really? What are the different […]
How to Spot a Phishing Email: 7 Red Flags & Real Examples

In our last guide, What is Phishing?, we explained how hackers use deceptive messages to trick you into giving up your sensitive information. Now, it’s time to move from theory to practice. How do you identify these malicious emails in your own inbox? The good news is that most phishing attacks aren’t as clever as […]
What is Phishing? A Beginner’s Guide to the #1 Cyber Threat

You’ve likely heard the term “phishing” before, but what does it actually mean? It’s more than just a spam email; it’s the single most common and dangerous threat that the average person will face online. Understanding what phishing is, how it works, and why criminals use it is the first and most important step in […]
What Is a Black Hat Hacker?

Who Are Black Hat Hackers? A Look at the Bad Guys of Cybersecurity In our previous posts, we’ve explored the basics of cybersecurity and met the “good guys”—the ethical White Hat hackers who work to protect our digital world. But to be a great defender, you have to understand your adversary. It’s time to step […]
Types of Cloud Computing Models Explained Simply
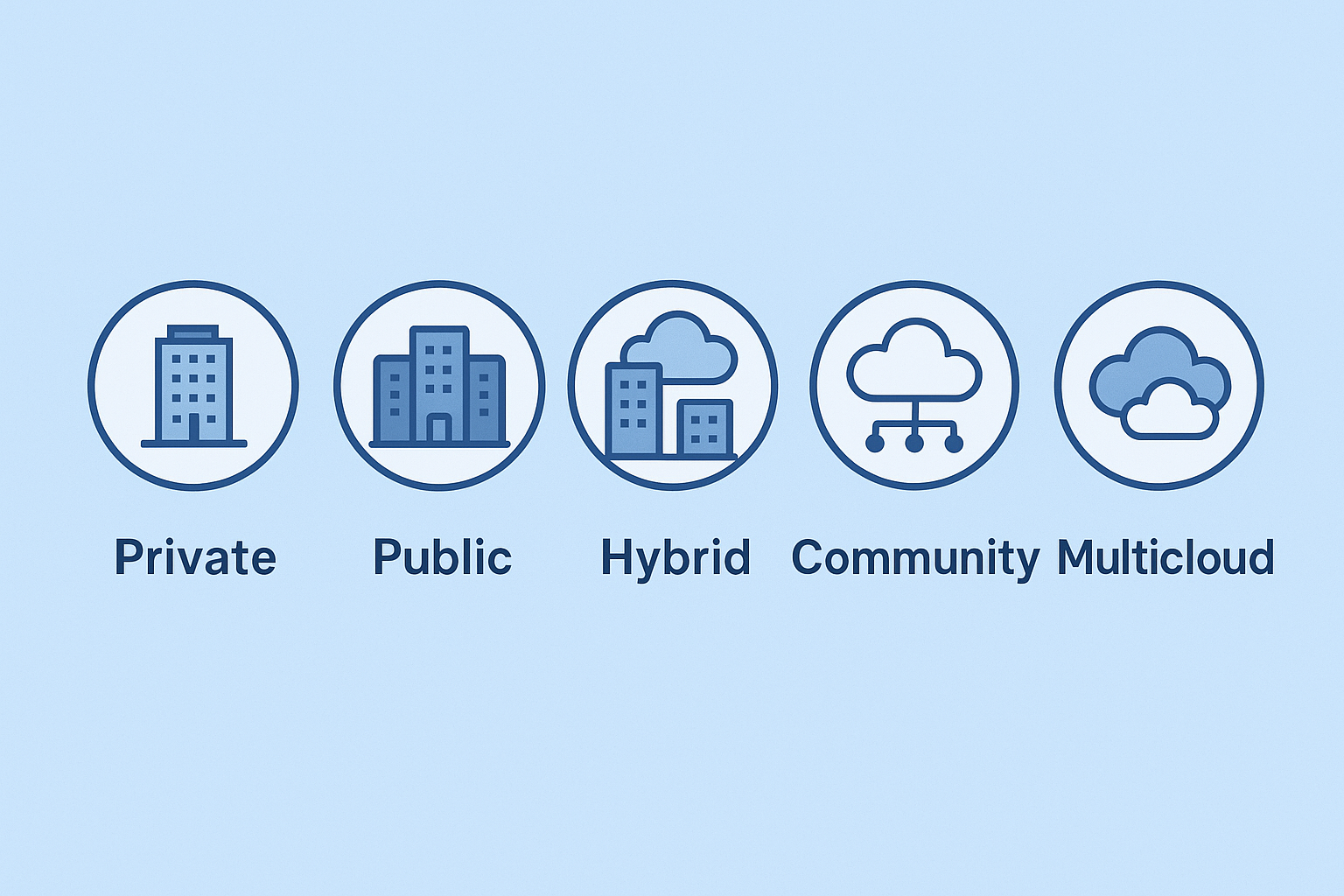
The world of cloud computing is filled with acronyms. IaaS, PaaS, SaaS, DBaaS, Hybrid, Multicloud—it can feel like learning a new language. But understanding this language is the key to making smart decisions about technology, security, and architecture. Consider this your definitive translation guide. In this article, we will provide clear, practical definitions for every […]
What is Cloud Computing? Explained with Pros & Cons
“The Cloud” is one of the most dominant terms in technology, but what does it actually mean to move to the cloud? Is it always the right decision? While the cloud offers incredible power, using it is a strategic choice with both massive benefits and critical trade-offs. This article will serve as your first clear-headed […]
