OSI Model Layer 1: The Physical Layer (Cables, Signals & Bits)
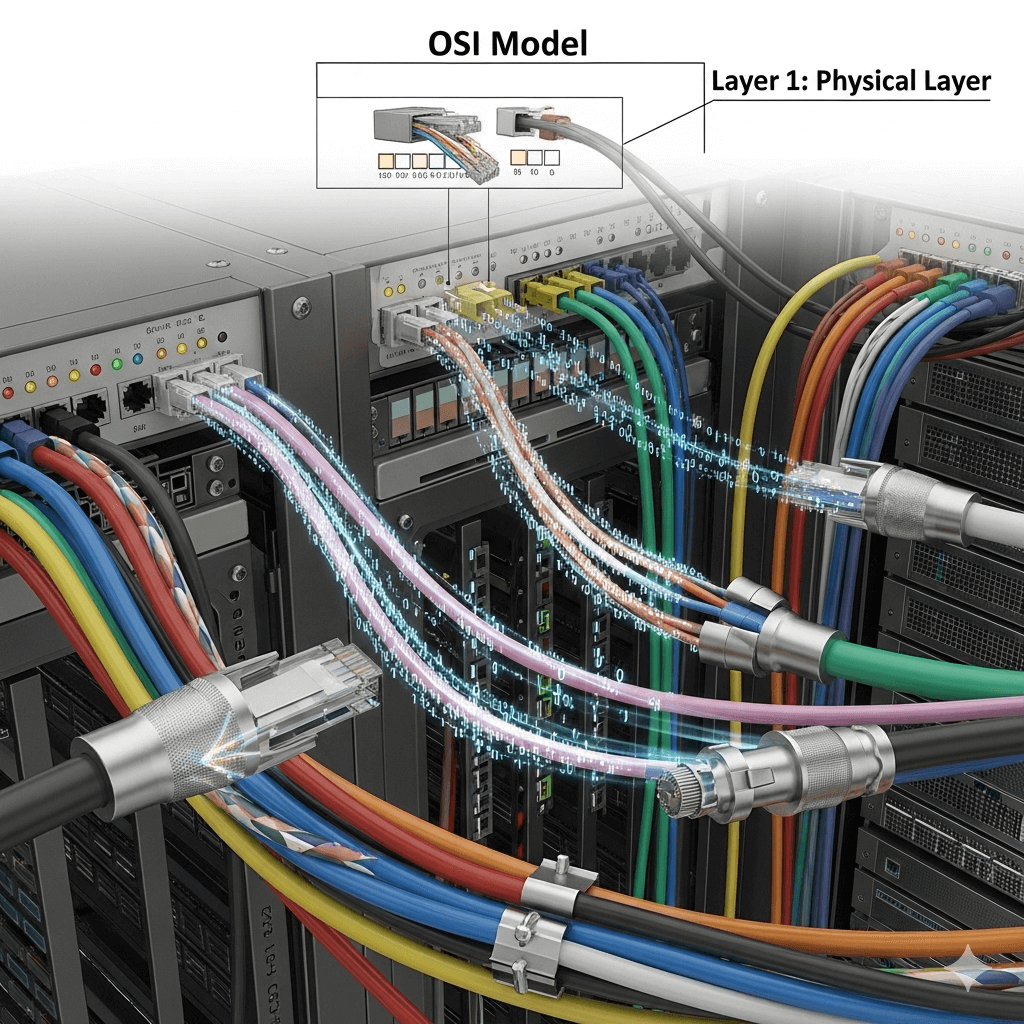
We’ve completed an incredible journey through the OSI Model! We’ve seen applications create data, the Presentation Layer (Layer 6) format it securely, the Session Layer (Layer 5) manage conversations, the Transport Layer (Layer 4) ensure reliable delivery, the Network Layer (Layer 3) route it globally, and the Data Link Layer (Layer 2) handle local transfers. […]
OSI Model Layer 3: The Network Layer (IP Addressing & Routing)
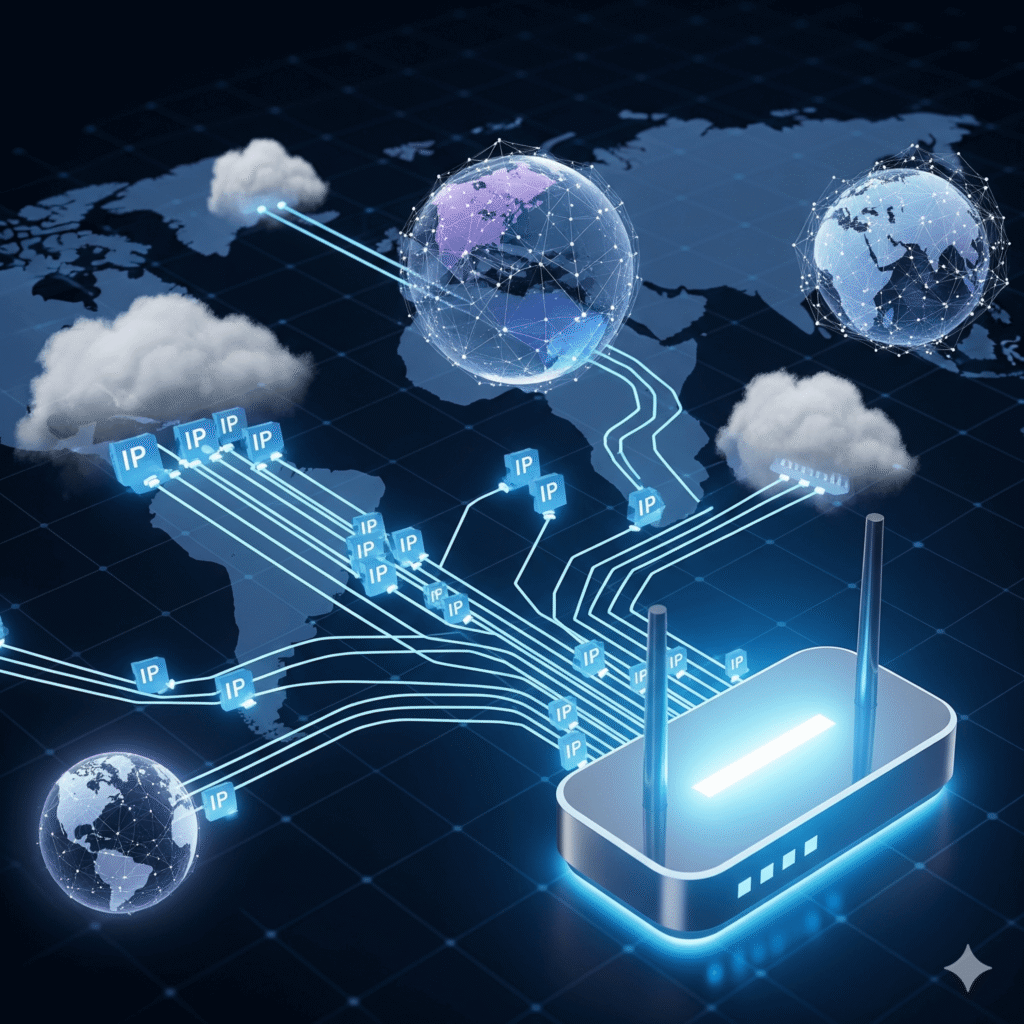
In our last post, we saw how the Transport Layer (Layer 4) prepares our data for its end-to-end journey. But how does that data find its way through the vast, interconnected maze of networks that make up the internet? That’s the mission of Layer 3: The Network Layer. Think of this layer as the global […]
The Transport Layer Explained: How Data Moves Reliably Online
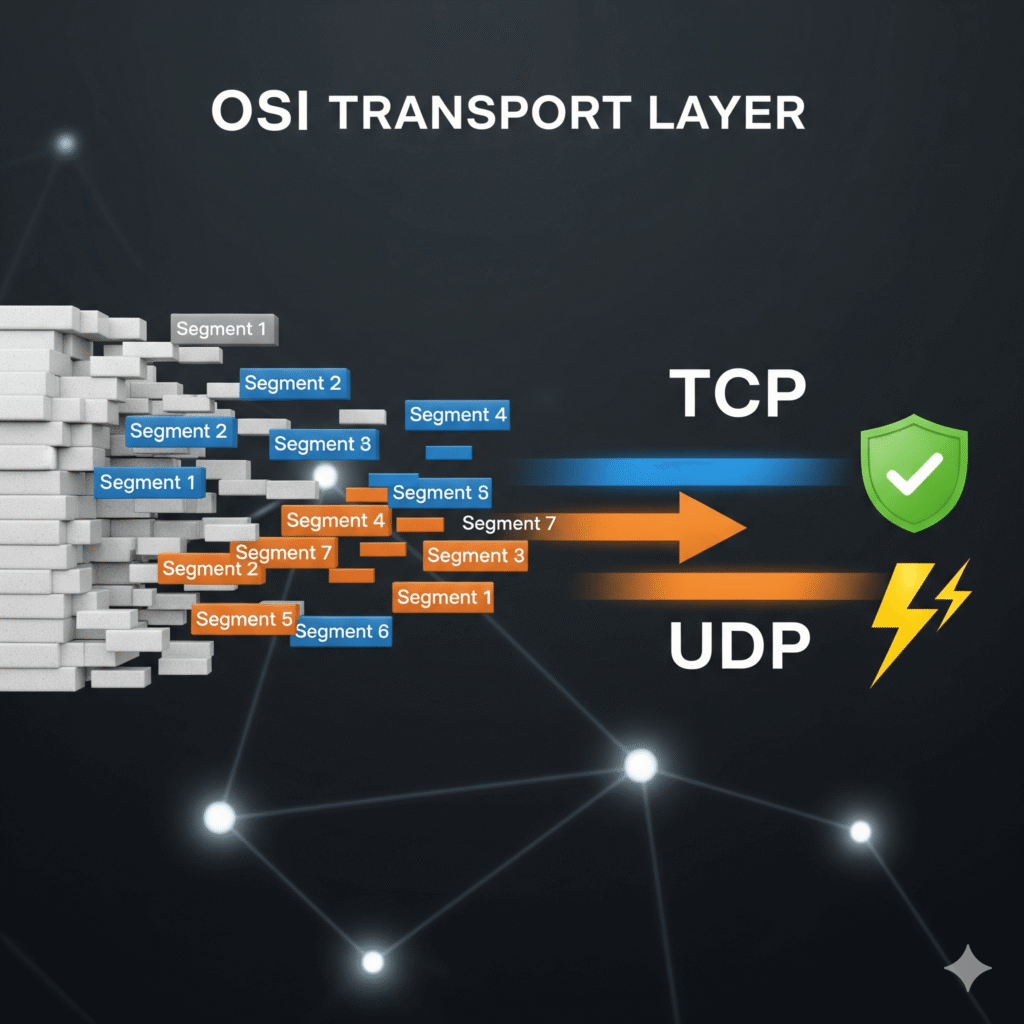
In our last post, we saw how the Session Layer (Layer 5) establishes and manages the conversation between two applications. But once that conversation is open, how do we actually send the data back and forth reliably? That’s the crucial job of Layer 4: The Transport Layer. Think of the Transport Layer as the network’s […]
OSI Model Layer 5: A Simple Guide to the Session Layer
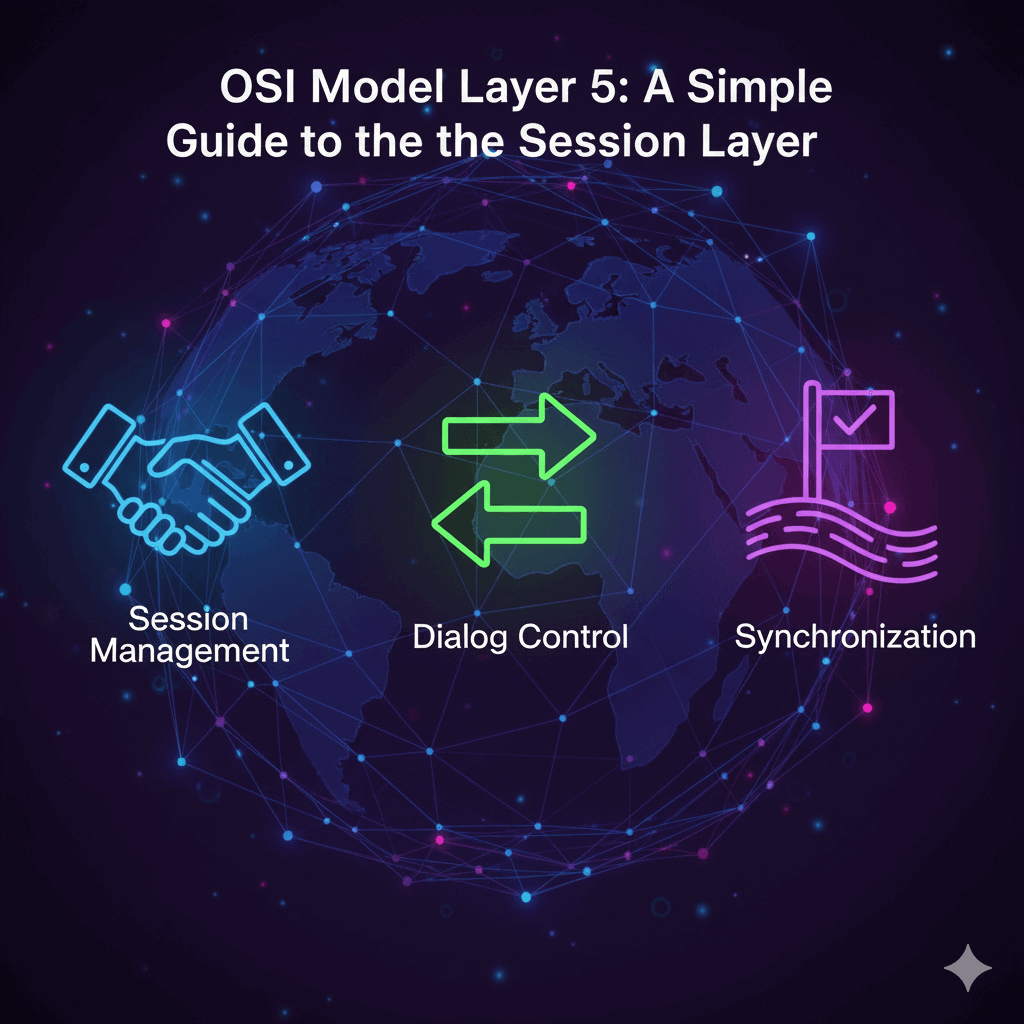
In our last post, we explored how the Presentation Layer (Layer 6) acts as a universal translator, formatting our data securely. Now that our data is ready, it’s time to establish a connection and manage the conversation. Welcome to the engine room of network dialogue: Layer 5, the Session Layer. If the Application Layer is […]
The Top 5 Entry-Level Cybersecurity Certifications to Get Hired

You’ve read the roadmap and you’re ready to start your journey into cybersecurity, but one question looms large: “Which certification should I get first?” With dozens of options available, the path forward can seem confusing. Don’t worry, we’re here to clear things up. A certification is more than just a piece of paper; it’s a […]
What is Social Engineering? (The Art of Human Hacking)
What is a hacker’s single most effective tool? It’s not a complex piece of code or a supercomputer. It’s the human mind. The art of exploiting human psychology to bypass security is called Social Engineering, and it’s often the first step in a major cyberattack. In our previous lessons, we’ve talked about what malware is […]
How to Use VirusTotal: A Beginner’s Guide to Checking Files & Links
You’ve just received a strange email with an attachment you weren’t expecting. You know from our guide to spotting phishing attacks that you should never open it blindly. So, what’s the next step? Before you delete it, you can investigate it like a security professional. The first and most important tool for this job is […]
The 5 Best Cybersecurity Books for Beginners (2025 Reading List)

Online courses and hands-on labs are essential for learning practical skills, but some of the best foundational knowledge still comes from well-written books. For anyone new to the field, finding the best cybersecurity books for beginners can be a challenge, as the market is flooded with thousands of options. To help you get started, we’ve […]
What Does a Firewall Protect Against? (A Simple Guide)

You’ve probably heard that you need a firewall to be safe online, but what does a firewall actually do? Think of a firewall as the security guard standing at the gate of your computer network. Its only job is to inspect every piece of data trying to get in or out and decide if it’s […]
What is Microsoft Azure? A Beginner’s Guide

In our last guide, we explored the dominant leader of the cloud market, Amazon Web Services (AWS). But the world of cloud computing is not a one-horse race. The fastest growing and most powerful challenger is Microsoft Azure. Azure is the cloud computing platform from Microsoft, and it has become the backbone for countless businesses, […]
