The Top 5 Entry-Level Cybersecurity Certifications to Get Hired

You’ve read the roadmap and you’re ready to start your journey into cybersecurity, but one question looms large: “Which certification should I get first?” With dozens of options available, the path forward can seem confusing. Don’t worry, we’re here to clear things up. A certification is more than just a piece of paper; it’s a […]
What is Social Engineering? (The Art of Human Hacking)
What is a hacker’s single most effective tool? It’s not a complex piece of code or a supercomputer. It’s the human mind. The art of exploiting human psychology to bypass security is called Social Engineering, and it’s often the first step in a major cyberattack. In our previous lessons, we’ve talked about what malware is […]
The 5 Best Cybersecurity Books for Beginners (2025 Reading List)

Online courses and hands-on labs are essential for learning practical skills, but some of the best foundational knowledge still comes from well-written books. For anyone new to the field, finding the best cybersecurity books for beginners can be a challenge, as the market is flooded with thousands of options. To help you get started, we’ve […]
What Does a Firewall Protect Against? (A Simple Guide)

You’ve probably heard that you need a firewall to be safe online, but what does a firewall actually do? Think of a firewall as the security guard standing at the gate of your computer network. Its only job is to inspect every piece of data trying to get in or out and decide if it’s […]
What is a Brute Force Attack? (A Simple Explanation & How to Stop It)
Imagine a thief trying to open a bicycle lock. Instead of skillfully picking it, they simply sit down and try every single possible combination, starting from 0000, then 0001, 0002, and so on. Given enough time, they are guaranteed to find the right code. This is exactly how a brute force attack works in the […]
What is the Cyber Kill Chain?
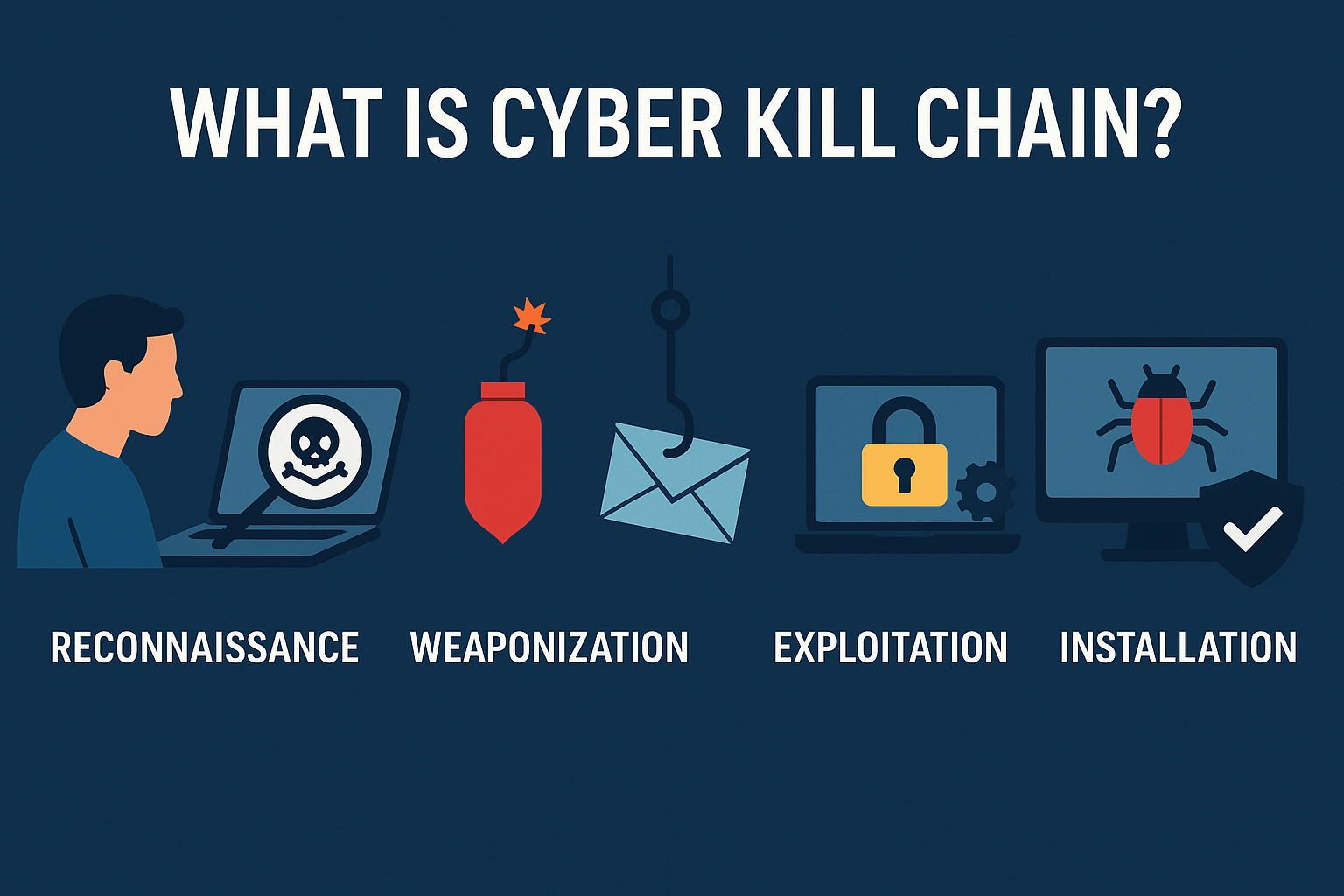
A successful cyberattack isn’t a single event; it’s a carefully planned campaign with multiple, distinct stages. To defend against an enemy, you must first understand how they think and operate. This is where the Cyber Kill Chain comes in. The Cyber Kill Chain is a framework originally created by defense company Lockheed Martin that outlines […]
