A successful cyberattack isn’t a single event; it’s a carefully planned campaign with multiple, distinct stages. To defend against an enemy, you must first understand how they think and operate. This is where the Cyber Kill Chain comes in.
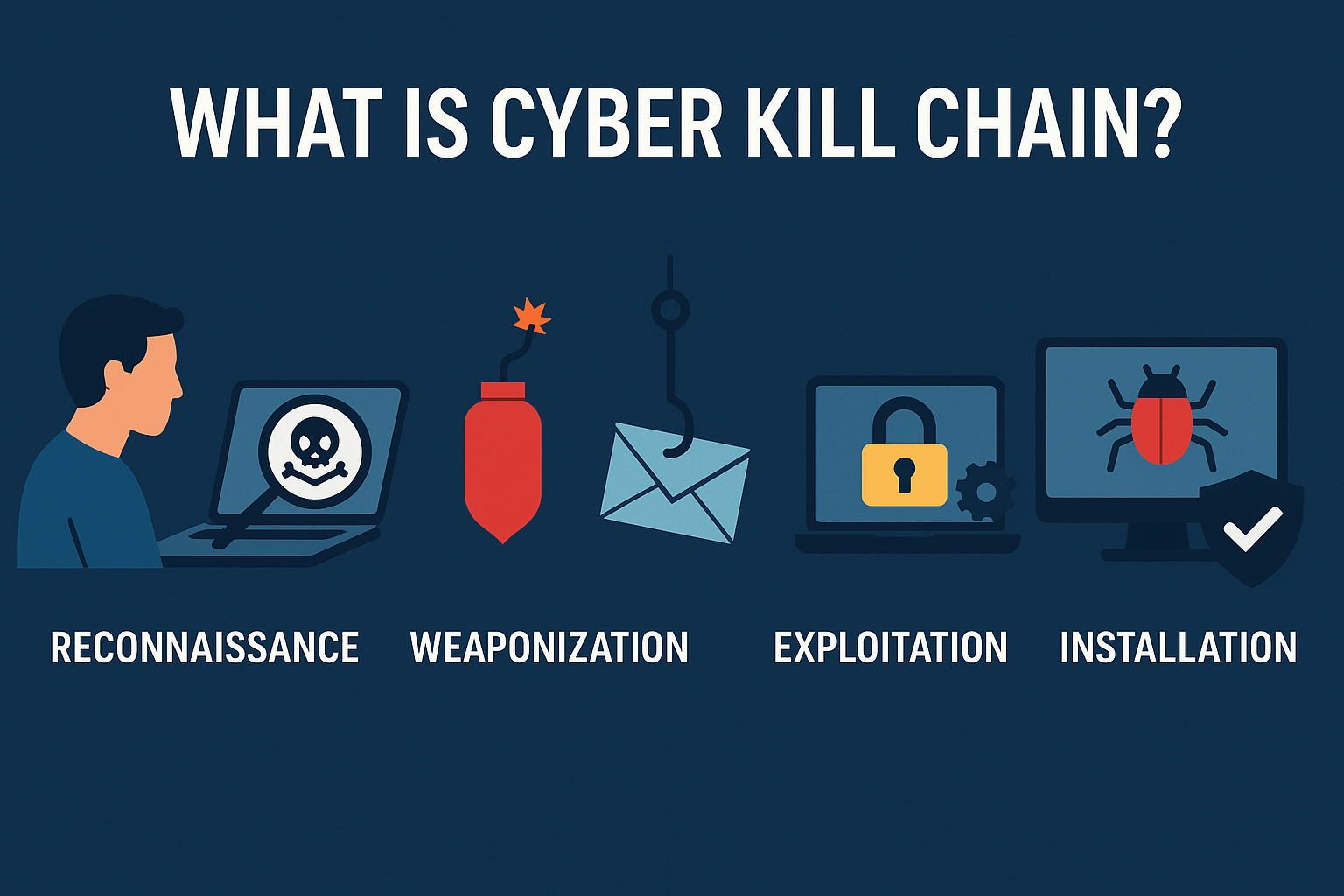
The Cyber Kill Chain is a framework originally created by defense company Lockheed Martin that outlines the 7 typical stages of a cyber intrusion. By understanding these steps, security professionals can learn where and how to “break the chain” and stop an attack in its tracks. For a beginner, it’s the best way to deconstruct a hack and understand the attacker’s methodology.
The 7 Steps of the Cyber Kill Chain
Let’s walk through each stage of a typical cyberattack, from initial planning to the final objective.
Step 1: Reconnaissance (The Spying Phase)
This is the information-gathering phase. Before launching an attack, a hacker will research their target to find potential weaknesses. This isn’t active hacking; it’s passive spying. They might:
- Scan for open network ports.
- Browse employee profiles on LinkedIn to find targets for emails.
- Identify what server software or plugins a website is using to look for known vulnerabilities.
Step 2: Weaponization (Building the Trap)
Once the attacker has identified a weakness, they create a malicious payload tailored to exploit it. This often involves combining a malicious program with a seemingly harmless delivery vehicle. For example, they might embed malware into a PDF or Microsoft Word document, or craft a convincing phishing email with a link to a malicious website.
Step 3: Delivery (Launching the Attack)
This is the step where the attacker sends their weapon to the target. The delivery method is chosen based on the reconnaissance from Step 1. The most common delivery methods include:
- Phishing emails sent to employees.
- Infected USB drives left in a public area.
- A “watering hole” attack, where a website trusted by the target is compromised.
Step 4: Exploitation (Springing the Trap)
The weapon is triggered. This is the moment the attack becomes active. Exploitation occurs when the victim takes an action that enables the attacker’s code to run. This could be:
- Clicking a malicious link in a phishing email.
- Opening an infected email attachment.
- Visiting a compromised website that exploits a vulnerability in the victim’s browser.
Step 5: Installation (Gaining a Foothold)
Once the system is exploited, the malware installs itself onto the victim’s computer. The goal of this stage is to achieve persistence, meaning the malware will survive even if the computer is rebooted. This gives the attacker a reliable, long-term foothold inside the network.
Step 6: Command & Control (C2) (Phoning Home)
With the malware installed, it opens a “Command and Control” channel, essentially “phoning home” to a server controlled by the attacker. This C2 channel allows the hacker to remotely issue commands to the compromised computer, turning it into a controllable asset.
Step 7: Actions on Objectives (The Goal)
With persistent access and remote control, the attacker can finally carry out their ultimate goal. This is the “Actions on Objectives” phase. The objective could be anything, such as:
- Data Exfiltration: Stealing sensitive files, intellectual property, or customer data.
- Destruction: Wiping hard drives or corrupting critical systems.
- Ransom: Encrypting files and demanding a payment (ransomware).
How Defenders Use the Kill Chain
The true power of this model is for defense. By understanding that an attack is a sequence of events, a defender only needs to break the chain at one single point to be successful.
- By training employees to spot phishing emails, you can break Step 3 (Delivery).
- By using antivirus software to block a malicious file, you can break Step 5 (Installation).
- By using a firewall to block the “phone home” connection, you can break Step 6 (Command & Control).
Conclusion: Thinking Like an Attacker to Build a Better Defense
The Cyber Kill Chain is an essential mental model that helps us understand that cyberattacks are a process, not a single, magical event. By breaking down the methodology of an attacker, we can better appreciate the importance of the layered defenses and security habits we’ve discussed throughout this course.
Ready to get your hands dirty? Subscribe to CyberTerminal to stay updated!
[INSERT_ELEMENTOR id=”1346″]